244: Victory From The Jaws Of Defeat
/Topics:
-This week we are proud to be sponsored by FLEXdesk, an offering from our friends at Rooted Consulting. FLEXdesk - Help Desk support that grows with you
-Sam shares a story where a client has some confusion with hardware
-Social media and clients. Do they mix?
-Joe shares a story about a client calling and saying the keyboards were not working at their retail store so they couldn't check out customers. We walked through looking for a battery compartment or a way to plug them in, but they didn't seem to have any way to change batteries or charge them. Then Joe remembered that the Logitech keyboards are solar powered and wonders if something changed in the environment. Client said they recently replaced all the lights with energy efficient LEDs! Apparently the new LED lights are so efficient, they don't have any spare light to charge the keyboards (or more likely, they aren't the right wavelength of light to work with the solar panels).
-Sam talks about voice recognition when meeting someone in person
-After upgrading a hard drive on a 27" iMac, Sam realizes he needed to fix the hinge. He found an excellent option from The Mac Hack. As it turns out, a site that Joe knows well.
-Joe investigates a situation where sent mail doesn't show in the client's Sent mailbox. Mail.app was configured to BCC the client on all emails, and Gmail was deleting the copy from his Sent when the copy in the Inbox was deleted.
-Sam recounts being at JFK Airport in New York City when the emergency alert system was used to warn of a water main break in the next terminal and wonders if iBeacon was used to alert only people in the airport.
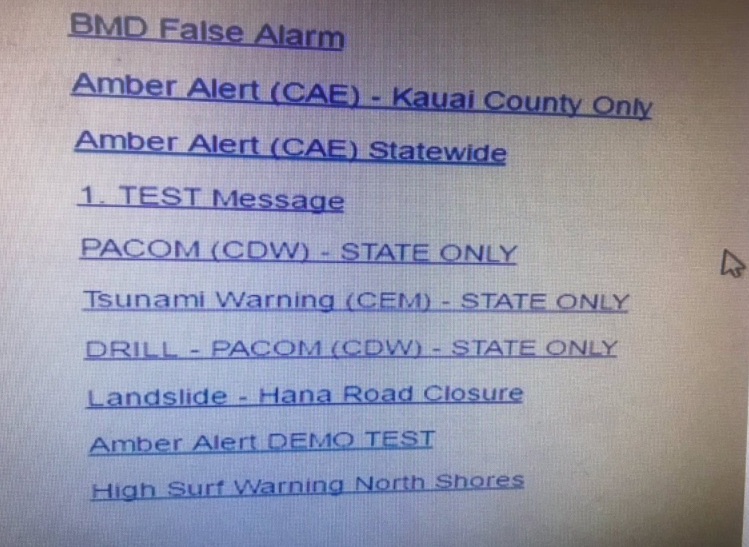
-We discuss the recent false alarm in Hawaii which also used the emergency alert system, and while Joe can't help but introduce a conspiratorial angle, it was likely due to bad design. Perhaps Heinlein's Razor (or Hanlon's Razor) – "Never attribute to malice that which is adequately explained by stupidity" – applies here.
-followup on Episode 236: MacBook Pro - Turn Back Time re: Temp user can not be deleted. Joe noticed that when migrating to a clean install of 10.13.2, Migration Assistant prompts to re-enter some users' passwords. For non-admin users, it changes passwords to a temporary password (looks like one generated by Keychain Assistant) and then prompts the user to change it upon first login. Could this be related to the root login issue? And/or to Joe’s Temp user issue? Note the difference in behavior when using Reset Password vs. Change Password. Joe bets that it's related to the method of storing the password hash – maybe there’s a less secure format for legacy accounts with longstanding passwords, which Apple has now deprecated?